Required SAP authorizations for Studio
The authorizations that you need for Studio 12.1.x depend on whether you are using the Transaction module or the Query module.
The Studio 12.x modules for Transaction and Query fully protect SAP® security features. In no circumstances can the Transaction and Query modules override the SAP authorization restrictions that you are bound to.
In most cases, these SAP authorizations are already in place. If, however, you have tried the Transaction module or the Query module but cannot use it, or if you are seeing error messages, the information below can help you and your security team to understand the SAP authorization required to work with the Transaction and Query modules and address the issue.
Transaction: Required SAP authorizations
Customers running SAP with Basis level 700 Support Pack stack 24 or higher will need to implement the custom Winshuttle Function Module for Non-Batch recording modes to work.
Transaction authorization via SAP GUI:
The Transaction module cannot run a transaction if you cannot run that transaction in the SAP GUI. If you do not have access to a particular transaction, please obtain authorization for it before you record or run that transaction in the Transaction module.
Remote Function Calls (RFC) authorization:
The Transaction module makes RFC calls to SAP. You must have this additional access assigned to you. In most cases, these authorizations are already assigned to you. The following objects with the indicated values should be in your SAP user profile for working with the Transaction module.
For the S_RFC authorization object:
• Field RFC_TYPE Value FUGR (function group)
• Field ACTVT Value 16 (execute) or *
• Field RFC_NAME
The following values are required for running shuttle files: SYST, SRFC, SUSR, RFC1, RFCH, SBDC, ATSV, STTF, SDTX
The following additional values are required for recording shuttle files: SBDR, SCAT, STTM, SDTX
The following values are required to use document attachment: BDS_BAPI
Additionally, it requires access to object S_BDS_DS with all values except lock and delete.
The following value is required to use SAP List of Values (F4) with forms: SWFMOD_Workflow
The following values are required for Addin F4 help: RHF4
The following values are required for WFM v11:
WFM rfms self check: /WINSHTLQ/*
F4 in WFM: SIMG, BDL5
Record in WFM: SBDR, SCP2
Record, User Format in WFM: RFC1, SU_USER
Background Query run in WFM: BDL3, THFB
Calculate prices BAPI call in WFM: WVK8
Vendor master functionality call via Direct in WFM: FIN_AP_AR_BANK, 1011, BAPT, 1013
Customer master functionality call via Direct in WFM: SZAK
InfoSet SQ02, Queries SQ01 in WFM: AQCF
To check if a user is authorized to use a given rFM, the Transaction module validates that the user has EXECUTE(16) permission on the Function Group. Accordingly, when a given Function Module executes, it accesses the structures defined in the Function group too, so authorization for the Function Group is needed.
The Authority_Check rFM validates whether the user is authorized to use the Function Module of a given Function Group.
Table Level authorizations:
The Transaction module can get logs, extended comments, field descriptions, and messages during the debug process. For this, the user must have access to certain tables. Table level access is controlled by authorization object S_TABU_DIS. Transaction needs access to the following tables: T100, TFDIR, DD03L, DD04L, TSTCT, D020T, and DD03M. To enable this access, please set up the following authorization:
Authorization Object: S_TABU_DIS
Field Authorization Group (DICBERCLS) = SS, &NC&
Field Activity (ACTVT) = 03 (Display only)
Transaction (non-WFM)
| Table name | Purpose |
| TSTCT | Get description of transaction code |
| D020T | Get description of screen |
| DD03M | Get field description |
| TFDIR | Check that Debug mode is supported |
| T100 | Extracting message |
| DD03L | Retrieve data types corresponding to fields |
GUI Scripting authorizations:
In addition to RFC calls, the Transaction module also provides access to the SAP system using the SAP GUI Scripting mode. To check whether GUI scripting is enabled, look on the right-end of the SAP GUI status bar.
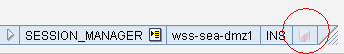
If you see the barber-pole icon on your status bar, GUI scripting is enabled.
If you do not see the icon, ask your security team to use the RZ11 transaction to enable GUI scripting. To enable SAP GUI scripting on the SAP server, the administrator must set the profile parameter sapgui/user_scripting to TRUE on the application server. To enable this parameter, run transaction RZ11. See OSS note 480149 for specific information.
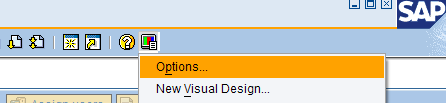
Additionally, please enable scripting on the SAP GUI front-end as follows:
- Open the Options dialog box from the main GUI screen.
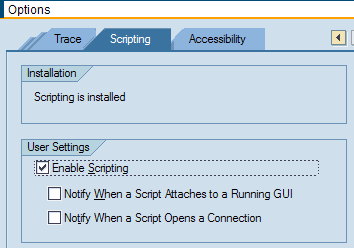
- Select the Scripting tab, and select the Enable Scripting check box.
SAP authorizations table
|
Function Group |
Instance |
Mode |
Description |
| SBDC | Run Run- Step-by-step | Batch | |
| Record | GUI Scripting for Ep Portal | ||
| Run | GUI Scripting for Ep Portal | ||
| ATSV | Run | Batch mode | |
| SUSR | Record | ||
| Run | |||
| SBDR | Record | Batch | |
| Record | Non-Batch without controls | ||
| Record | Non-Batch with controls | ||
| STTM | Record | Non-Batch with controls | |
| SCAT | Record | Non-Batch with controls | |
| STTF | Run | Non-Batch with controls | |
| Run | Non-Batch without controls | ||
| RFC1 | Record | ALL | Check presence of FMs before calling them |
| Run | ALL | ||
| RFC1 | Run | Non-Batch | |
| SDTX | Record | ALL | |
| Run | ALL | ||
| RHF4 | None | None | Addin F4 Help |
| /winshtl/txafugr | Record | ALL | First their existence checked and then only called |
| Run | ALL | ||
| /winshtl/txufugr | Record | ALL | First their existence checked and then only called |
| Run | ALL | ||
| SYST | Logon | ||
| SRFC | |||
| RFCH | |||
| Table | Instance | Mode | Comments |
| TSTCT | Record | ALL except GUI Scripting | Description of transaction code |
| D020T | Record | ALL except GUI Scripting | |
| DD03M | Record | ALL | |
| TFDIR | Run-Step-by-step mode | ALL | Called for SAP Release less than 45 |
| T100 | Run | ALL except GUI Scripting | |
| Run | BAPI with Extended Log |
Query: Required SAP authorizations
Remote Function Calls (RFC) authorization:
The Studio v12 Query module makes RFC calls to SAP. You must have this additional access assigned to you. In most cases, these authorizations are already assigned to you. The following objects with the indicated values should be in your SAP user profile for working with the Query module.
For the S_RFC authorization objects:
- Field RFC_TYPE: FUGR (function group)
- Field ACTVT: 16 (execute) or *
- Field RFC_NAME: *
Create and run: RFCH, RFC1, SRFC,SUSO,SUSR,SYST
F4 value – RHF4
Create and Run: SDIFRUNTIME
T-code recording to table SBDR, SDTX, SBDC,
InfoSets SQ02 and queries SQ01: INSTALL, AQRC
The following values are required for WFM v11:
WFM rfms self check: /WINSHTLQ/*
LDB process via WFM: SDIFRUNTIME
Orphaned Chunk clearing in WFM: SGWY
Table Level authorizations:
To access a specific table in the Query module, you need table-level access. Table-level access in SAP is independent of a transaction. For example, you may have access to the transaction MM01 which uses the Material Master table (MARA), but this does not give you automatic access to that table. Table-level access is controlled by the authorization object S_TABU_DIS for client dependent tables and by S_TABU_CLI for client independent tables.
Query non-WFM table names:
|
Table name |
Purpose |
| DD02T | Get SAP Table description |
| DD17S | Retrieve all fields corresponding to table |
| DD03L | Returns a data table having fields with key flag for given table |
| DD02L | Look for table type |
| DD02V | Look for table type and description from view. |
| DD27VV | Get all fields corresponding to view |
| DDFTX | To search table for field description |
Authorization object:
S_TABU_DIS
Fields:
Authorization group (DICBERCLS): &NC&
Activity (ACTVT): 03 (Display)
For example:
Almost every client-dependent table in SAP is assigned to a specific authorization group in the SAP table TDDAT, field CCLASS. For example, the table MARA is assigned to the authorization group MA.
To access Table MARA, authorization group MA must be assigned to your SAP profile in the authorization object S_TABU_DIS as indicated below:
Authorization object:
S_TABU_DIS
Fields:
Authorization group (DICBERCLS): MA (For table MARA)
Activity (ACTVT): 03 (Display)
Notes
- Each table can belong to a different authorization group. For you to access different tables, your profile must have the proper authorization for the appropriate groups.
- For client-independent tables (where field ‘MANDT’ is not present in the table), you need the following authorization object in your SAP profile:
Authorization Object:
S_TABU_CLI
Fields:
CLIIDMAINT: X
- If your required table is not listed in the SAP table TDDAT, you can attain the specific authorization group by assigning the following:
Authorization object:
S_TABU_DIS
Fields:
Authorization group (DICBERCLS): &NC&
Activity (ACTVT): 03 (Display)
