Using LDAP or Active Directory for Authentication
Spectrum™ Technology Platform can be configured to use an LDAP or Active Directory server for authentication. When a user logs in to Spectrum™ Technology Platform, the user's credentials are verified using LDAP or AD. The system then checks to see if there is a Spectrum™ Technology Platform user with the same name. If there is, the user is logged in. If there is not, then a Spectrum™ Technology Platform user account is automatically created for the user and given the role user.
The following diagram illustrates this process:
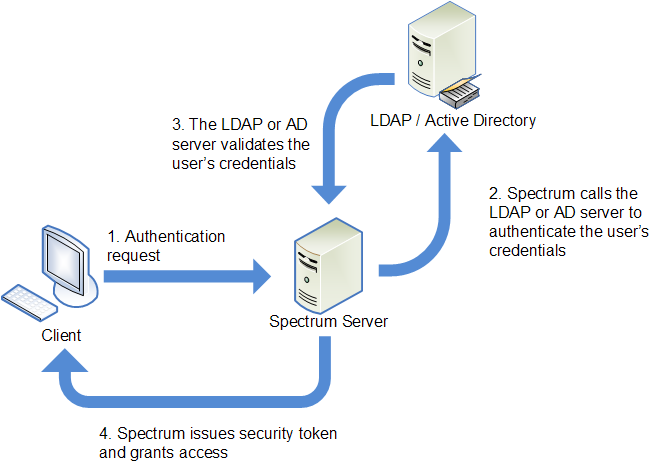
Before configuring Spectrum™ Technology Platform to use a directory service for authentication, confirm that your directory service meets these requirements:
- For LDAP, the directory server must be LDAP Version 3 compliant.
- There are no specific requirements for the Active Directory server.
If you are running Spectrum™ Technology Platform in a cluster, you must modify the spectrum-container.properties file and the spectrum-config-ldap.properties file on each of the servers in the cluster. Stop the server before modifying the file, then start the server after you are done modifying the file. If you mapped an LDAP attribute value to a role, this mapping will replicate to all nodes in the cluster, so you do not need to repeat the mapping procedure in the JMX console.