Disabling Host Checks in Token Authentication
In token authentication, the Spectrum Technology Platform server examines the token presented by the client before responding to the request. The server checks the token to see if it has expired, if it is encrypted correctly, and if it is from the correct host. For session tokens, the server also checks the session ID. If any of these checks fail, the token is rejected and the server does not respond to the request.
In a clustered environment, it is possible that requests may be redirected in a way that makes the request appear to be coming from a different host than is specified in the token, resulting in "invalid token" errors. For example, say you have a cluster with two nodes as shown here:
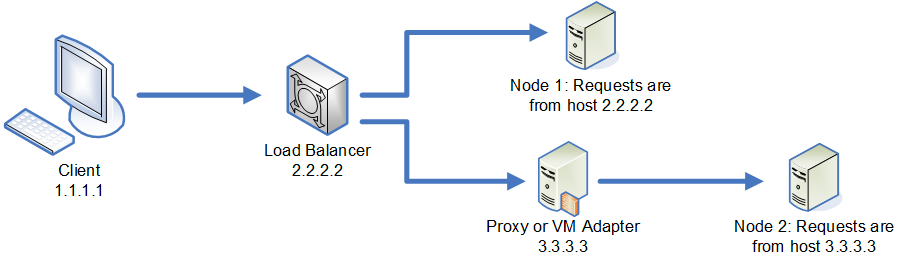
Let's say that the client makes a request and is the request is routed to Node 1. A token is created and tied to host 2.2.2.2 (the load balancer) since the node views the request as coming from the load balancer. If the next request from the client is routed to Node 2, the token will still be tied to host 2.2.2.2 but the request will appear to be coming from the proxy server, 3.3.3.3. In this case the node will reject the token because it appears that it is not associated with the host making the request.
In this situation you must configure the Spectrum Technology Platform server to ignore the host information included in the token. This should only be done if you have an environment where there are different network devices between the load balancer and the nodes. If all nodes are behind the same network device, there is no need to disable the host check.