Applies to:
- Winshuttle Foundation
Verify that Kernel Mode Authentication is Disabled
To verify that kernel mode authentication is disabled on both servers:
- Open the IIS manager.
- Select the IIS web site to verify.
- In Features View, under IIS, double-click the Authentication icon.
- Select Windows Authentication and ensure that it is enabled.
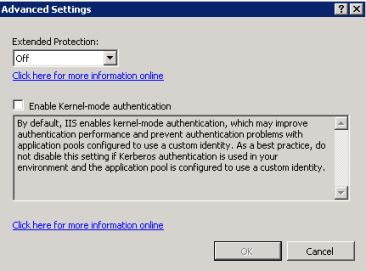
- Click Advanced Settings.
- Verify that both EAP and Kernel Mode Authentication are disabled.
Ensuring clients can connect to Kerberos ports on the Active Directory role
Back to topTo use Kerberos authentication, clients will have to request ticket-granting tickets (TGT) and service tickets (ST) from the Key Distribution Center (KDC) over UDP or TCP port 88. By default, when you install the Active Directory Role in Windows Server 2008 and later, the role will configure the following incoming rules to allow this communication by default:
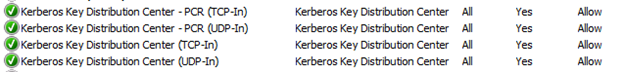
- Kerberos Key Distribution Center – PCR (TCP-In)
- Kerberos Key Distribution Center – PCR (UDP-In)
- Kerberos Key Distribution Center (TCP-In)
- Kerberos Key Distribution Center (UDP-In)
In your environment ensure these rules are enabled and that clients can connect to the KDC (domain controller) over port 88.
Test browser authentication
Back to topAfter configuring the Active Directory, DNS, and SharePoint Server you can now test whether Kerberos authentication is configured correctly by browsing to your web applications. When testing in the browser, ensure the following conditions are met:
- The test user is logged into a Windows XP, Windows Vista, or Windows 7 computer joined to the domain that SharePoint Server is installed in, or the test user is logged into a domain trusted by the SharePoint Server domain.
- The test user is using Internet Explorer 7.0 or later (Internet Explorer 6.0 is no longer supported in SharePoint Server 2010). See Plan browser support (SharePoint Server 2010).
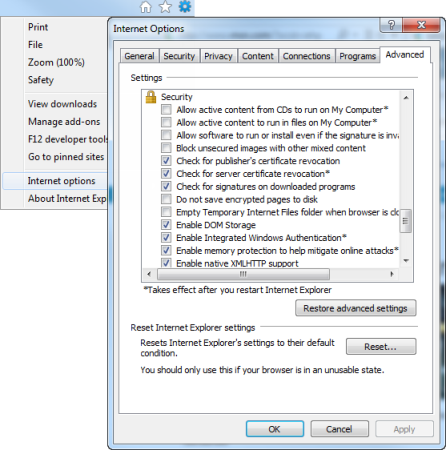
- Integrated Windows authentication is enabled in the browser. On the Tools menu in Internet Explorer, click Internet Options. Click the Advanced tab and ensure that Enable Integrated Windows Authentication* is enabled in the Security section:
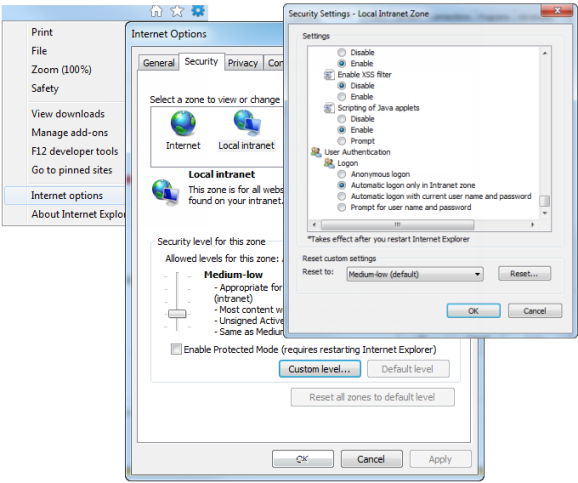
- Local intranet is configured to automatically logon clients. On the Tools menu in Internet Explorer, click Internet Options. Click the Security tab, click the Local Intranet icon, and click Custom level. Scroll down and ensure that Automatic logon only in Intranet zone is selected.
Note: It is possible to configure automatic logon on other zones, but the topic of IE security zone best practices is outside the scope of this guide. In this example, the intranet zone will be used for all tests.
- Ensure that Automatically detect intranet network is selected. On the Tools menu in Internet Explorer, click Internet Options. Click the Security tab, click Local Intranet, and then click Sites.
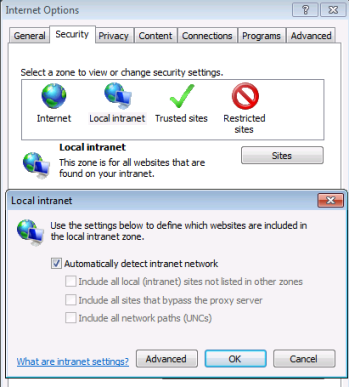
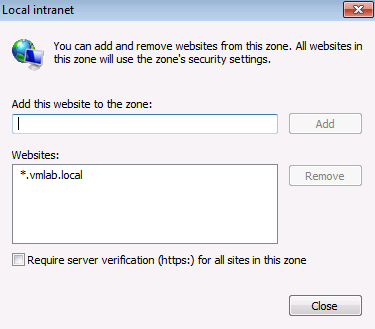
- If you are using fully qualified domain names to access the SharePoint Server web applications, ensure that the FQDNs are included in the intranet zone, either explicitly or by wildcard inclusion (for example, "*.vmlab.local").
Once the previous conditions have been met, the easiest way to determine if Kerberos authentication is being used is by logging into a test workstation and navigating to the web site in question. If the user isn't prompted for credentials and the site is rendered correctly, you can assume Integrated Windows authentication is working. The next step is to determine if the negotiate protocol was used to negotiate Kerberos authentication as the authentication provider for the request. This can be done by checking the server security logs in the following way:
Viewing Security Logs
Back to topIf Kerberos authentication is working correctly, you will see Logon events in the security event logs on the front-end webs with event ID = 4624.
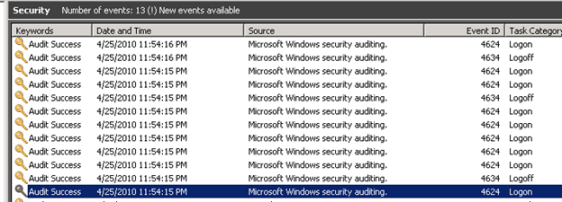
In the general information for these events you should see the security ID being logged onto the computer, as well as the Logon Process used, which should be Kerberos.
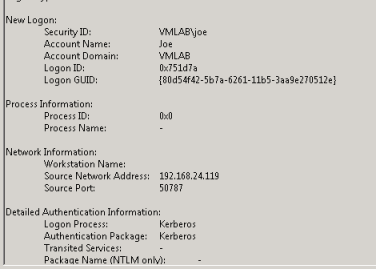
Kerberos should now be fully authenticated and included in your environment.
If you need help
Back to topIf, after you add Kerberos to your environment, CENTRAL and Workflow do not work correctly, contact Winshuttle Support at info@winshuttle.com.